
How was it possible to break the Enigma in spite of such a lot of possible settings?
Enigma Codes could have been unbreakable with the methods available at the time. The Germans believed, that it never was possible to find the correct Enigma settings for a ciphered message, even if the enemy has exactly the same machine. They also modified the machine from time to time.
But operator errors and laziness allowed the Poles, and later the British, to crack the code.
To understand this we have to explain how a message was sent :
Basic settings (Wheel order, Rings, Stecker) were written down in a code book, and changed daily. Different parts of the army uses different code books.
The operator selects 3 letters randomly (e.g. FRX) and sets the starting position (Grundstellung) with these letters. Then another operator selects again 3 letters at random (This was the "message key" =Spruchschlüssel: e.g. AGI) and typed it twice (e.g. AGIAGI) . Sending it twice was done to avoid any transmission errors, if letters have been lost. The random selection of the message key should prevent any statistical analysis on the data, but offers possibility for human errors.. The actual message was coded with this message key( e.g.AGI ).
Here is an example :
This text was sent: At the beginning was some plain text (date, time, number of letters...) The first 6 letters are the enciphered message key, written twice.
+ HRKM 13617 1807 - AN HEERESGRUPPENKOMMANDO 2= 2109 -1750 - 3 TLE - FRX FRX - 1TL -172=
HCALN UQKRQ AXPWT WUQTZ KFXZO MJFOY RHYZW VBXYS IWMMV WBLEB DMWUW BTVHM RFLKS DCCEX IYPAH RMPZI OVBBR VLNHZ UPOSY EIPWJ TUGYO SLAOX RHKVC HQOSV DTRBP DJEUK SBBXH TYGVH GFICA CVGUV OQFAQ WBKXZ JSQJF ZPEVJ RO
Note : AXPWT was an identifier key added to the message.
Deciphering of the text was done in reverse way.
A message should not be longer than 200 characters. Longer messages were split up into pieces with different keys. The letter combination CH was abbreviated (abgekürtzt) by Q, words have been separated by X. Numbers have to be spelled out.
1929 the Poles knew about the commercial Enigma and hired three mathematicians for code breaking. The most famous was Marjan Rejewski.
It is not quite clear how the Poles got all details about the military Enigma. Different stories are told. They collected a lot of German messages and have been supported by the French secrete service with copies of Enigma training handbooks got by espionage. With all this information they have been able to rebuild an Enigma until 1933. The correct rotor wiring was found by help of mathematical equations (Gleichung).
The Poles also found out, that the double coded message key at the beginning of each message sometimes leads to identical letters, called "females" (.e.g ABCABC enciphers to PSTPWA, letter 1 and 3 is supposed to be the same letter). This occurred on average every 25 messages.
They developed different devices and methods to find the message keys:
Zygalski, one of the mathematicians, used perforated paper sheets and arranged them on an illuminated table to reveal possible starting states.
The "Bomba" was a mechanical device simulating the 26*26*26 positions of the 3 Enigma rotors. 6 "Bomba's" were necessary for the 6 possible wheel orders (3 wheels until 1939).
Over the years, the Germans did modifications on the messages and the machine itself. They added 2 additional wheels, used more Sockets, the twice given encoded message key was given up in 1940, the wheel order was changed daily (starting from 1937, not only every 3 months). After these changes the Poles didn't have enough money and resources to built 60 new Bombas which became necessary to break the modified Enigma.
In 1939 the Polish mathematicians moved to France, at least they gave all their knowledge and material to the British.
It is said that the British have decoded 200.000 - 500.000 German messages during the war. How was it possible to decipher these amount of messages?
What are the weaknesses? For better understanding I have to explain
The operator has to select 3 letters randomly But sometimes they use "AAA", "BBB" or the diagonals of the keyboard (QFL), any abbreviations, his own initials or any dirty words.
A German operator in southern Italy has used frequently his girlfriend initials CILLI and the British called such bad and easy to guess keys CILLIES (sometimes also called Sillies = Dummheiten)
If you type a "A" you will get any letter from B-Z, but never an ``A''. The sequence : AAAAAAA may be XUVGFXY without any ``A''.
A tired German operator has been told to send out dummy messages and he typed only the last letter of the keyboard : ``L''. The British code breaking expert immediately recognized the missing ``L'' in the enciphered message and they got a very big crib (see below).
A crib is a part of the plain text which is known to correspond with a part of the code.
Knowing the source of the message (army, navy) you can guess the meaning.
For instance most of the messages start with AN (e.g AN GENERAL ...) . This was coded as ANXGENERAL
Another possibility was : AN DIE GRUPPE (to the group) The code breakers tested the first 3 letters for ANX.
KEINEBESONDERENEREIGNISSE (no special occurrences, nothing to report)
could be a part of the message This crib was placed above the enciphered text
and moved left and right until no letter enciphers to itself.
Wheels 4 1 5 Start X C D Rings A X U Stecker "EZBLXP"
crib: KEINEBESONDERENEREIGNISSE
cipher: JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
plain: ANMARTINOBERZALEKXKEINEBESONDERENEREIGNISSEINDERBULMEHEUTE
================================================================
.KEINEBESONDERENEREIGNISSE position : 2
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
...KEINEBESONDERENEREIGNISSE position : 4
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
.......KEINEBESONDERENEREIGNISSE position : 8
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
............KEINEBESONDERENEREIGNISSE position : 13
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
..................KEINEBESONDERENEREIGNISSE position : 19
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
ANMARTINOBERZALEKXKEINEBESONDERENEREIGNISSEINDERBULMEHEUTE<<<<<<<
........................KEINEBESONDERENEREIGNISSE position : 25
JWZBPNKPXGLFLINBQSRKRXMUDOEISVNMDUEXOXTGEMRXIZONKLGZVCHSYF
total sum of possible positions : 6 max : 33
A kiss is a message that has been sent previously on a lower level radio net, which has already been enciphered. This means, the same message was send twice, but with different systems.
The British forced such messages by doing any military activity and then they waited for the messages. They bombed a LEUCHTTONNE and then they tested the Enigma messages for a ERLOSCHENISTLEUCHTTONNE crib.
Found codebooks of sunken submarines or captured weather ships and military bases were also very helpful and provided the British with Enigma ground settings for some months and abbreviations for weather reports, which could be used as cribs. Some of these keys has also been used by the U-Boots.
Bletchley Park was the Government Communication Headquarters, located about 40 miles to the north of London and employed about 10,000 people at the end of the war. (Some sources also say 30,000 people.)

There have been 200 crypto analysts from universities. The most famous among them were Alan Turing and Gordon Welchman, two mathematicians.
The whole area was divided into different sections (huts = Baracke) with different responsibilities for naval and army Enigma messages. All messages were got by radio transmission received from different areas in Great Britain and sent to Bletchley Park. Incoming messages have been sorted by clerks and provided for decoding. The code name for the whole organization was ULTRA.
After the Polish had done that much quality work on Enigma the British could start developing their own Bomba. Called Bomb. It is said that the name comes from the clicking sound that the Bombe made when working on a crib, much like a timer bomb fuse.
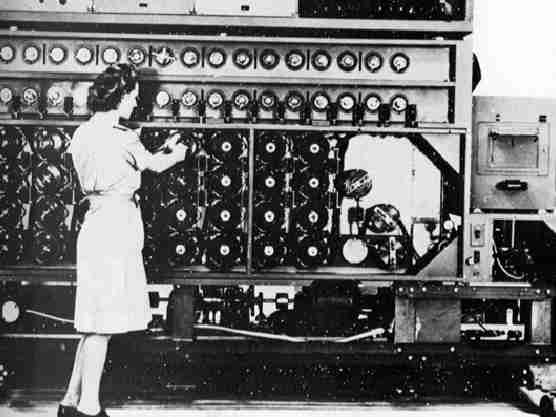
The Turing Bomb is a electromechanical machine and was in principal invented by the famous Alan Turing who is the father of the computer.
The size of the bomb is about 2.1 * 2 * 0.6 meter and cost 100,000 Pounds. It weights a ton. The central part of machine are the 36 rotors which represent twelve three-wheel Enigmas. The rotors had the same wiring as the Enigma wheels and could be exchanged. All rotors were driven by a motor. Each rotor has 104 contacts (26*4) which are connected together.
The purpose of the Bomb was the testing if the crib fits to the given message. The machine simple tries all 26*26*26 possible cases. If a possible key was found the bomb stopped. The correctness of the key was tested on a normal Enigma manually.
But the wheel order had to be still guessed and the crib finding had to be also done by code breaking experts.
The first bomb was developed within 3 months and was finished in march 1940. The second in August.
At least 200 of these machines were built and located all over great Britain.
High speed bombs for the naval Enigmas were built in USA.
The German never knew about the existence of the Turing Bomb and all the activities in Bletchley Park.
After the war the parts of the bombs were used for other purposes. No original bomb exists anymore, but there is a rebuild project. All stuff about the Enigma cracking was top secret up to 1975. In 1996, the Americans published secret documents concerning Turing's work on the Bomb. But some details have remained unknown until today.